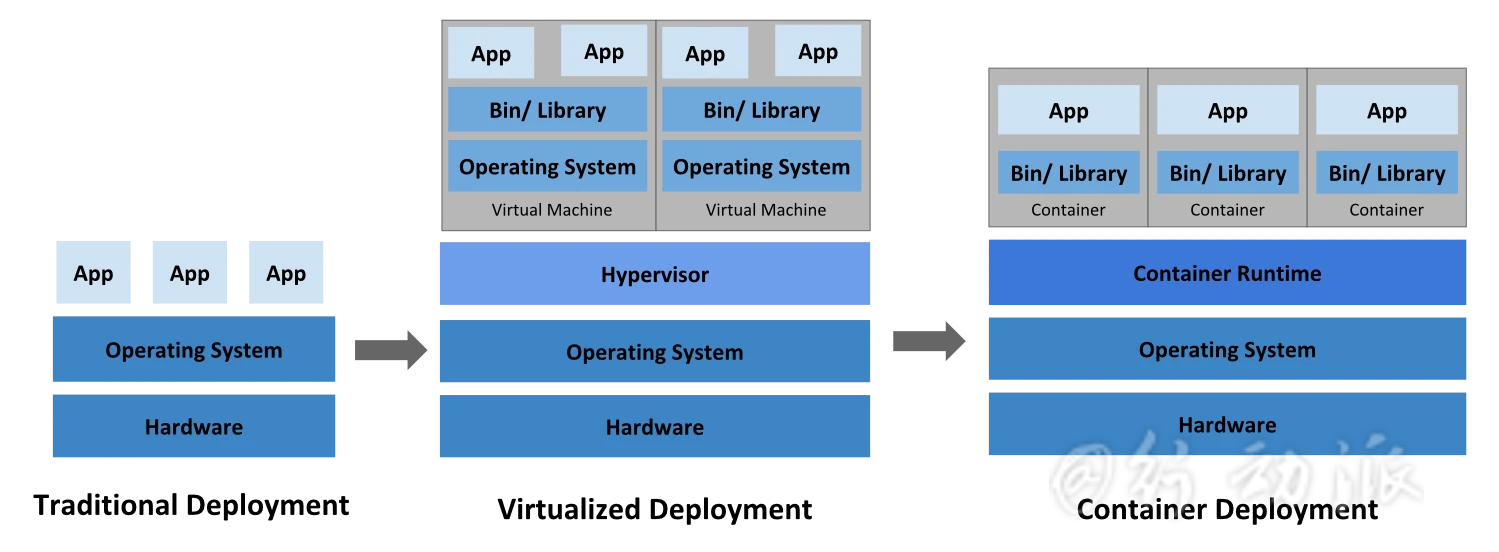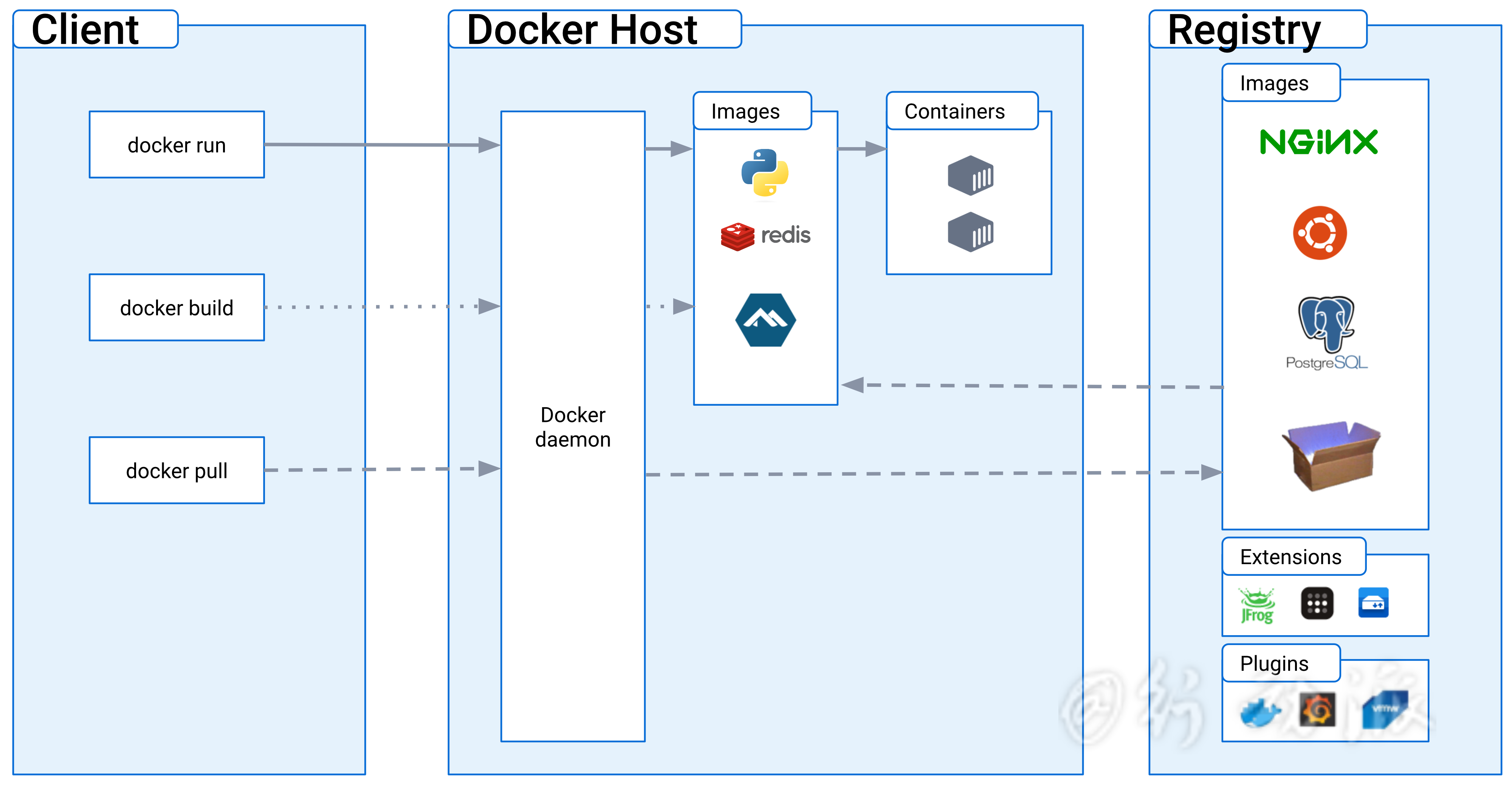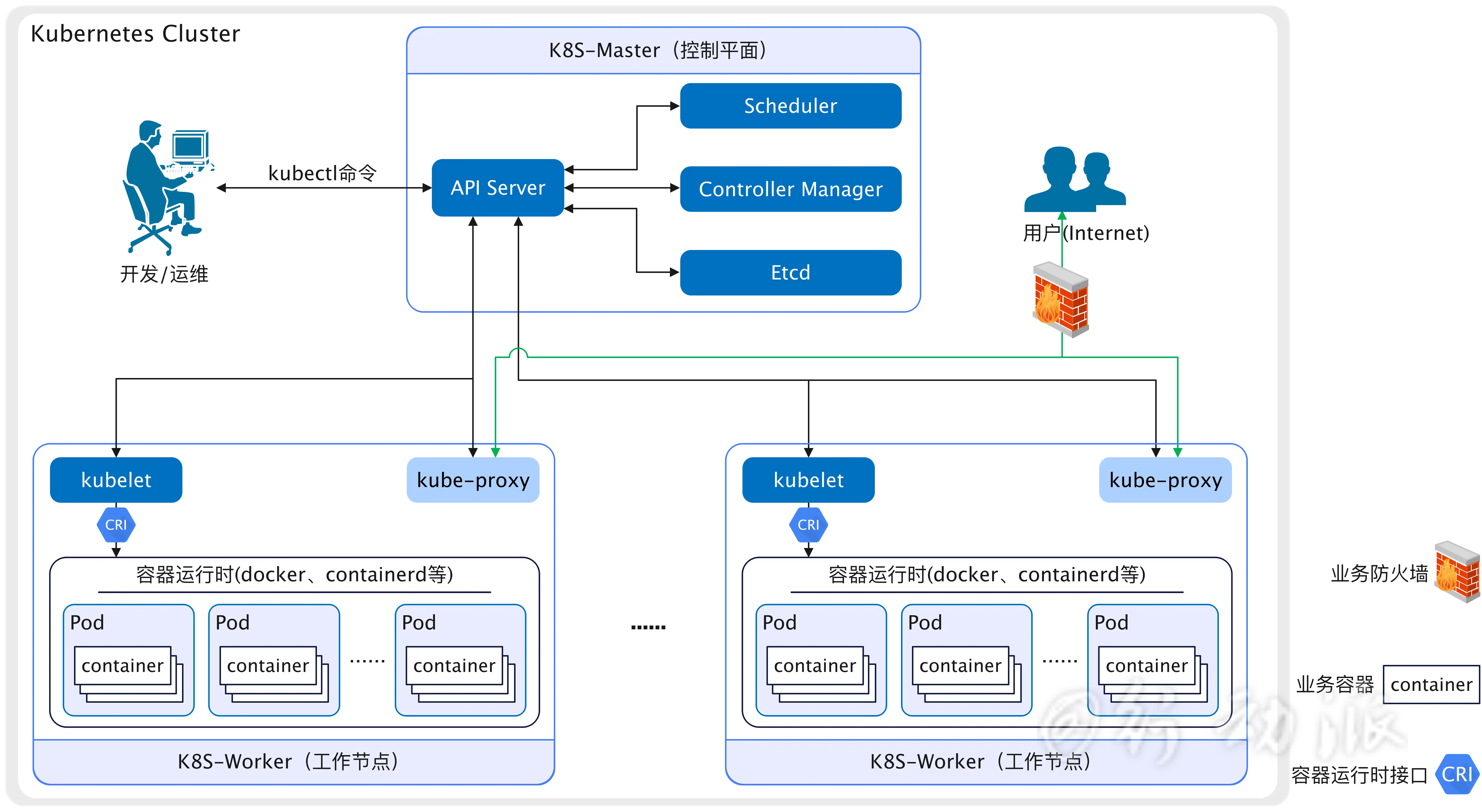
背景概述
需求:
最近学习cka认证知识,每个考题的开头都会使⽤“kubectl config use-context xxx”命令切换到对应的集群,可实现在一台电脑上管理多个集群,不需要ssh登录到各集群环境中,即安全又方便,完全可以运用在工作中。不过考试环境中已经配置好了,只需要上述命令切换即可,所以本篇文章主要研究如何实现kubectl管理多个集群。
原理:
k8s使用 kubeconfig 文件来组织有关集群、用户、命名空间和身份认证机制的信息。 kubectl 命令行工具使用 kubeconfig 文件来查找选择集群所需的信息,并与集群的 API 服务器进行通信。
基于上述的k8s机制,我们可以通过将新的集群、用户和上下文定义(context)添加在kubeconfig文件中,便可以使用 kubectl config use-context 命令快速地在集群之间进行切换。
kubeconfig文件
kubeconfig 文件说明
- kubeconfig文件默认是
$HOME/.kube/config,也能通过设置环境变量KUBECONFIG指定其它 kubeconfig 文件。 - kubeconfig 文件可以有多个,有多个时需要配置环境变量
KUBECONFIG,KUBECONFIG环境变量包含一个 kubeconfig 文件列表。此文件列表对于 Linux 和 Mac,列表以冒号分隔;对于 Windows,列表以分号分隔。 - kubeconfig配置一般通过
kubectl config view命令查看,有多个kubeconfig文件的情况下,此命令查看的是合并多个 kubeconfig 文件的结果。 - kubeconfig配置也可以直接查看kubeconfig文件,如
$HOME/.kube/config文件,此方式会显示证书、密码等base64加密后的详细信息
注意:用于配置集群访问的文件称为“kubeconfig 文件”,并不意味着有一个名为 kubeconfig 的文件
kubeconfig示例
# kubectl config view
apiVersion: v1
clusters: # 说明:集群,新增的集群会在这里
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://kubernetes.docker.internal:6443
name: docker-desktop
contexts: # 说明:上下文,新增的上下文会在这里
- context:
cluster: docker-desktop
user: docker-desktop
name: docker-desktop
current-context: docker-desktop
kind: Config
preferences: {}
users: # 说明:用户,新增的用户会在这里
- name: docker-desktop
user:
client-certificate-data: REDACTED
client-key-data: REDACTED配置对多集群的访问
配置说明:在MacBook安装kubectl命令工具(安装桌面版docker并启用kubernetes集群即可使用kubectl命令),以MacBook为管理机,添加远程k8s集群,此集群为cka练习环境。
1. 在远程集群准备配置信息
kubectl添加集群需要该集群的API Server 地址、集群ca证书(如果启用了https的话)、具有集群管理权限的 ServiceAccount 并拿到其 token
-
通过ssh登录cka练习环境集群的master节点
-
获取该集群的API Server 地址,本示例中该地址为“https://11.0.1.111:6443”
# kubectl cluster-info Kubernetes control plane is running at https://11.0.1.111:6443 CoreDNS is running at https://11.0.1.111:6443/api/v1/namespaces/kube-system/services/kube-dns:dns/proxy To further debug and diagnose cluster problems, use 'kubectl cluster-info dump'. -
获取该集群的ca 证书
# kubectl get secret $(kubectl get secrets | grep default-token | awk '{print $1}') -o jsonpath="{['data']['ca\.crt']}" | base64 --decode /-----BEGIN CERTIFICATE----- MIIC5zCCAc+gAwIBAgIBADANBgkqhkiG9w0BAQsFADAVMRMwEQYDVQQDEwprdWJl cm5ldGVzMB4XDTIxMDkwNjE0NTQxNFoXDTMxMDkwNDE0NTQxNFowFTETMBEGA1UE AxMKa3ViZXJuZXRlczCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAN3P J7HtI6mCCrkOlt/6Lw7zknHZtAuWswwACrLPkpJ8HgjcpO3px/am4wpmnBc0x7Xq hN0zww1uwHIbB2CUvisxPkgti6G6cHficWm3UhpYGP5nt8RYs9w4BhMF87omYYD/ R8vLzEcoA7nFbQasi0QucNxg/5xtGXvGSpS89exXneFqVfZc7gnSwGTtts9a4akm xK51lKYdIR8LBWyd5g7RvsLi8laqyKQ3uqcL33R0EIUwM1pNw/jCVIvn5e86vwb5 zc63FYB5KflukOQ7i8ewVWl3xSQMCpc0uzF+YYvQ3LxxMPoyDOQUcxYNuWKNhIsK PteeHmPC5225Sw18cCkCAwEAAaNCMEAwDgYDVR0PAQH/BAQDAgKkMA8GA1UdEwEB /wQFMAMBAf8wHQYDVR0OBBYEFBlqIebAIh92lvWw9+f0y+hUqvh+MA0GCSqGSIb3 DQEBCwUAA4IBAQAZQtxBLCZEgnKuVJ4N+TjQt3RCmweQfu/XxCBSfSRf+wxxOMKv SWijzUJu3tWvf9Exr5AhDeh1waF4PvXa4LRjK+LUS94yyqCQBFCbkrBqYeAOkK2B GG+JLTHDgRIboERPt3Bzj8fU6bw9EW5N3FmhVgG4Cl8abZiICoY11pVdXD4PGbYV BXKMKHjS6jGGzGEK7oskRlLfgtuHL9vC4C1pETzcQsmVCbdvl0vrsxNB0E8FpAfp R5iVSIqJK6Gm+2topgGfRW+6y7b5ljQkuCSbwZAbtJF3sHvsfvG9U1J8JcvaQWvR izONgr0uzuD0d6fdgBlk5Kbxm5nw4KVxrJnJ /-----END CERTIFICATE----- -
创建具有集群管理权限的 ServiceAccount 并拿到其 token(也可以使用现有的ServiceAccount ),本示例使用的用户名是 cka-admin
1)在kube-system的namespace中创建一个名为cka-admin的新服务帐户(ServiceAccount),使用kubectl create serviceaccount -h查看详细的命令格式及参数 # kubectl create serviceaccount cka-admin -n kube-system serviceaccount/cka-admin created 2)将已有的名为cluster-admin的ClusterRole绑定到新的服务帐户(ServiceAccount) cka-admin,使用kubectl create clusterrolebinding -h查看详细的命令格式及参数 # kubectl create clusterrolebinding cka-admin-binding --clusterrole=cluster-admin --serviceaccount=kube-system:cka-admin -n kube-system clusterrolebinding.rbac.authorization.k8s.io/cka-admin-binding created 3)获取cka-admin服务帐户的token # kubectl -n kube-system describe secret $(kubectl -n kube-system get secret | grep cka-admin | awk '{print $1}') Name: cka-admin-token-wwggv Namespace: kube-system Labels:Annotations: kubernetes.io/service-account.name: cka-admin kubernetes.io/service-account.uid: 6bc3c2ff-f488-48c8-9aac-56431b15a9de Type: kubernetes.io/service-account-token Data ==== namespace: 11 bytes token: eyJhbGciOiJSUzI1NiIsImtpZCI6IjFwRUlBVkVCeU5HSzdvY0YtdmE1a00yWXNMUDI4S1FFNW1Da29WYzZQeXcifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJja2EtYWRtaW4tdG9rZW4td3dnZ3YiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiY2thLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiNmJjM2MyZmYtZjQ4OC00OGM4LTlhYWMtNTY0MzFiMTVhOWRlIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmNrYS1hZG1pbiJ9.vGK0OPcBZyClTZrm6ELLP-ldrTXh2bc3GPB8SYn2K5JuIMD8bmWXAYUPc8DMu70z7eu_LqUmBXZv-EyVWwbcI-ouR01jKnnktW2Cfi6PrZEqFx7t5X-mzrjgqTxrAiyQYbffYI5nMh2_SBWVV3_1RqLJpmFqVXjLGA_A2Gm9GhJNzch47OYlp6us920A_s57kcv8CS-lzvLxwEnKpVBmyvaGWoRDlAWphxO33YRNrDYAdu5QINIcCVC1BrGDAQ8ZRQGVQQNes-J6Xdy1rfBCWHeegZePskc-kBvP_WJXiVZS6JSRJm7I76b40Yd0bGhmkif-0P5xH-pzI_llZqqWPw ca.crt: 1066 bytes
2. 管理机(MacBook笔记本)配置kubectl
-
将上述获取到的集群ca证书保存到MacBook笔记本的~/cka-ca.crt文件中
[wang@MBP2020 ~]% cat > ~/cka-ca.crt<<EOF -----BEGIN CERTIFICATE----- MIIC5zCCAc+gAwIBAgIBADANBgkqhkiG9w0BAQsFADAVMRMwEQYDVQQDEwprdWJl cm5ldGVzMB4XDTIxMDkwNjE0NTQxNFoXDTMxMDkwNDE0NTQxNFowFTETMBEGA1UE AxMKa3ViZXJuZXRlczCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAN3P J7HtI6mCCrkOlt/6Lw7zknHZtAuWswwACrLPkpJ8HgjcpO3px/am4wpmnBc0x7Xq hN0zww1uwHIbB2CUvisxPkgti6G6cHficWm3UhpYGP5nt8RYs9w4BhMF87omYYD/ R8vLzEcoA7nFbQasi0QucNxg/5xtGXvGSpS89exXneFqVfZc7gnSwGTtts9a4akm xK51lKYdIR8LBWyd5g7RvsLi8laqyKQ3uqcL33R0EIUwM1pNw/jCVIvn5e86vwb5 zc63FYB5KflukOQ7i8ewVWl3xSQMCpc0uzF+YYvQ3LxxMPoyDOQUcxYNuWKNhIsK PteeHmPC5225Sw18cCkCAwEAAaNCMEAwDgYDVR0PAQH/BAQDAgKkMA8GA1UdEwEB /wQFMAMBAf8wHQYDVR0OBBYEFBlqIebAIh92lvWw9+f0y+hUqvh+MA0GCSqGSIb3 DQEBCwUAA4IBAQAZQtxBLCZEgnKuVJ4N+TjQt3RCmweQfu/XxCBSfSRf+wxxOMKv SWijzUJu3tWvf9Exr5AhDeh1waF4PvXa4LRjK+LUS94yyqCQBFCbkrBqYeAOkK2B GG+JLTHDgRIboERPt3Bzj8fU6bw9EW5N3FmhVgG4Cl8abZiICoY11pVdXD4PGbYV BXKMKHjS6jGGzGEK7oskRlLfgtuHL9vC4C1pETzcQsmVCbdvl0vrsxNB0E8FpAfp R5iVSIqJK6Gm+2topgGfRW+6y7b5ljQkuCSbwZAbtJF3sHvsfvG9U1J8JcvaQWvR izONgr0uzuD0d6fdgBlk5Kbxm5nw4KVxrJnJ -----END CERTIFICATE----- EOF -
在Kubeconfig中设置集群条目:使用上述获取到的集群api server 地址与 ca 证书信息增加集群,注意ca证书的路径,如果下述命令不在ca证书文件所在的路径执行,请使用绝对路径
[wang@MBP2020 ~]% kubectl config set-cluster cka --server=https://11.0.1.111:6443 --certificate-authority=cka-ca.crt --embed-certs=true Cluster "cka" set. -
在kubeconfig中设置用户条目:本示例以cka-admin服务账户的token设置连接集群,使用kubectl config set-credentials -h查看详细命令格式及参数
[wang@MBP2020 ~]% kubectl config set-credentials cka-admin --token=eyJhbGciOiJSUzI1NiIsImtpZCI6IjFwRUlBVkVCeU5HSzdvY0YtdmE1a00yWXNMUDI4S1FFNW1Da29WYzZQeXcifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJja2EtYWRtaW4tdG9rZW4td3dnZ3YiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiY2thLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiNmJjM2MyZmYtZjQ4OC00OGM4LTlhYWMtNTY0MzFiMTVhOWRlIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmNrYS1hZG1pbiJ9.vGK0OPcBZyClTZrm6ELLP-ldrTXh2bc3GPB8SYn2K5JuIMD8bmWXAYUPc8DMu70z7eu_LqUmBXZv-EyVWwbcI-ouR01jKnnktW2Cfi6PrZEqFx7t5X-mzrjgqTxrAiyQYbffYI5nMh2_SBWVV3_1RqLJpmFqVXjLGA_A2Gm9GhJNzch47OYlp6us920A_s57kcv8CS-lzvLxwEnKpVBmyvaGWoRDlAWphxO33YRNrDYAdu5QINIcCVC1BrGDAQ8ZRQGVQQNes-J6Xdy1rfBCWHeegZePskc-kBvP_WJXiVZS6JSRJm7I76b40Yd0bGhmkif-0P5xH-pzI_llZqqWPw User "cka-admin" set. -
在kubeconfig中设置context(上下文)条目:使用kubectl config set-context -h查看详细命令格式及参数
[wang@MBP2020 ~]% kubectl config set-context cka --cluster=cka --user=cka-admin Context "cka" created. -
kubectl添加远程集群管理完成,查看最终的kubeconfig文件
[wang@MBP2020 ~]% kubectl config view apiVersion: v1 clusters: - cluster: # 新增的远程集群 certificate-authority-data: DATA+OMITTED server: https://11.0.1.111:6443 name: cka - cluster: certificate-authority-data: DATA+OMITTED server: https://kubernetes.docker.internal:6443 name: docker-desktop contexts: - context: # 新增的context(上下文) cluster: cka user: cka-admin name: cka - context: cluster: docker-desktop user: docker-desktop name: docker-desktop current-context: docker-desktop # 当前的context为docker-desktop,可使用kubectl config use-context命令切换 kind: Config preferences: {} users: - name: cka-admin # 新增的用户 user: token: REDACTED - name: docker-desktop user: client-certificate-data: REDACTED client-key-data: REDACTED
最终效果
-
查看当前context的集群信息
[wang@MBP2020 ~]% kubectl cluster-info Kubernetes control plane is running at https://kubernetes.docker.internal:6443 CoreDNS is running at https://kubernetes.docker.internal:6443/api/v1/namespaces/kube-system/services/kube-dns:dns/proxy To further debug and diagnose cluster problems, use 'kubectl cluster-info dump'. -
查看kubeconfig文件中的context,带“*”号的为当前的context
[wang@MBP2020 ~]% kubectl config get-contexts CURRENT NAME CLUSTER AUTHINFO NAMESPACE cka cka cka-admin * docker-desktop docker-desktop docker-desktop -
切换context
[wang@MBP2020 ~]% kubectl config use-context cka Switched to context "cka". -
查看切换context后集群信息
[wang@MBP2020 ~]% kubectl cluster-info Kubernetes control plane is running at https://11.0.1.111:6443 CoreDNS is running at https://11.0.1.111:6443/api/v1/namespaces/kube-system/services/kube-dns:dns/proxy To further debug and diagnose cluster problems, use 'kubectl cluster-info dump'.